IPsec
※ 基本要點 ※
Integrity (完整性): 訊息收發一致 [MD5, SHA]
Authentication (身份認證): 證明對方身份 [PSK, RSA, Key Management]
Confidentiality (加密): 隱藏訊息 [DES, 3DES, AES, SEAL]
IKEv1還是IKEv2?
IKEv1: Phase I 可選Main/Aggregate Mode,
IKEv2: Phase I 只有4 msg, 同時支援NAT-T,AES加密, EAP認證
※ IKEv1 Phase I ※
IKEv1 Phase I (Phase I 建立加密管道)(金鑰交換), udp500/4500:
設定IKE SA, SADB
想用Main Mode 定 Aggregate Mode?
Main Mode: 可以加密對家身份. 但6-ways handshake
Aggregate Mode: 3-ways handshake, 但不能加密對家身份, 都有hash
| ISAKMP Policy: IKE 用 ISAKMP framework 來交換SA ISAKMP [SA][ #包晒CIA加Group加Lifetime 加密Encryption: DES/3DES/AES; 認證Hash: MD5/SHA; 認證方式: pre-share key; DH-Group; 管道Lifetime ] ISAKMP [金鑰交換][ 認證密碼: Pre-Share Key ] | R1/R2(config)# crypto isakmp policy 1 R1/R2(config-isakmp)# encription aes R1/R2(config-isakmp)# hash md5 R1/R2(config-isakmp)# authentication pre-share R1/R2(config-isakmp)# group 2 R1/R2(config-isakmp)# lifetime 30000 R1(config)# crypto isakmp key 6 ccie address 192.168.23.2 R2(config)# crypto isakmp key 6 ccie address 192.168.13.1 |
※ IKEv1 Phase II ※
IKEv1 Phase II (Phase II 傳送加密Data)
設定Ipsec SA, SPD
只有Quick Mode
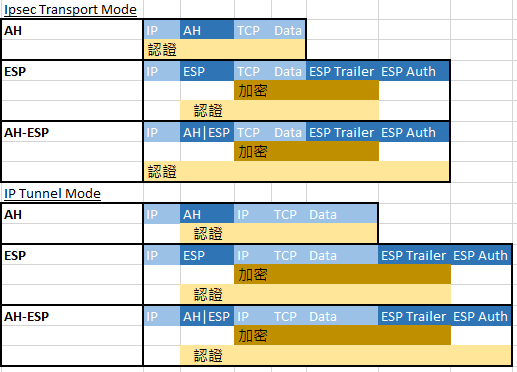
Transport Mode 定 Tunnel Mode?
Transport Mode: 只加密Data不加密IP, Internal用
Tunnel Mode: 加密Data又加密IP, 經Internet用
| Ipsec Policy: TRANSFORM SET (封裝)[ AH Transform; #AH只有認證 ESP Cipher; #ESP加密 ESP Auth; #ESP認證 Compression ] | R1/R2(config)# crypto ipsec transform-set TS esp-3des ah-sha-hmac |
| R1(config)# ip access-list extended VPN-Traffic R1(config-ext-nacl)# permit ip 192.168.10.0 0.0.0.255 192.168.20.0 0.0.0.255 R2(config)# ip access-list extended VPN-Traffic R2(config-ext-nacl)# permit ip 192.168.20.0 0.0.0.255 192.168.10.0 0.0.0.255 R1/R2(config)# crypto map CMAP 1 ipsec-isakmp R1(config-crypto-map)# set peer 192.168.23.2 R2(config-crypto-map)# set peer 192.168.13.1 R1/R2(config-crypto-map)# set transform-set TS R1/R2(config-crypto-map)# match address VPN-Traffic R1/R2(config)# int e0/0 R1/R2(config-if)# crypto map CMAP | |
| Verify | R1# show crypto isakmp sa R1# show crypto ipsec sa |
※ CA ※
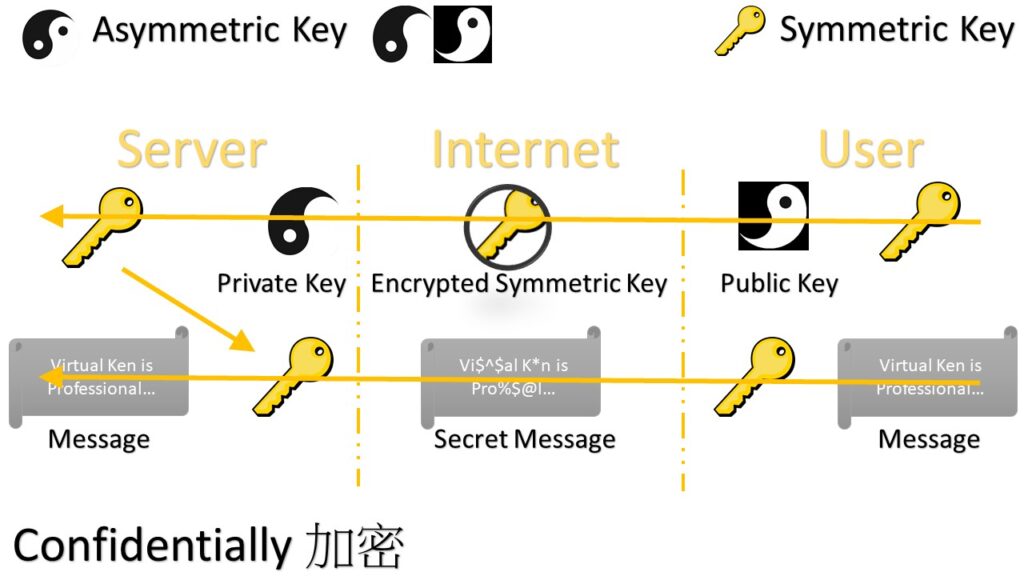
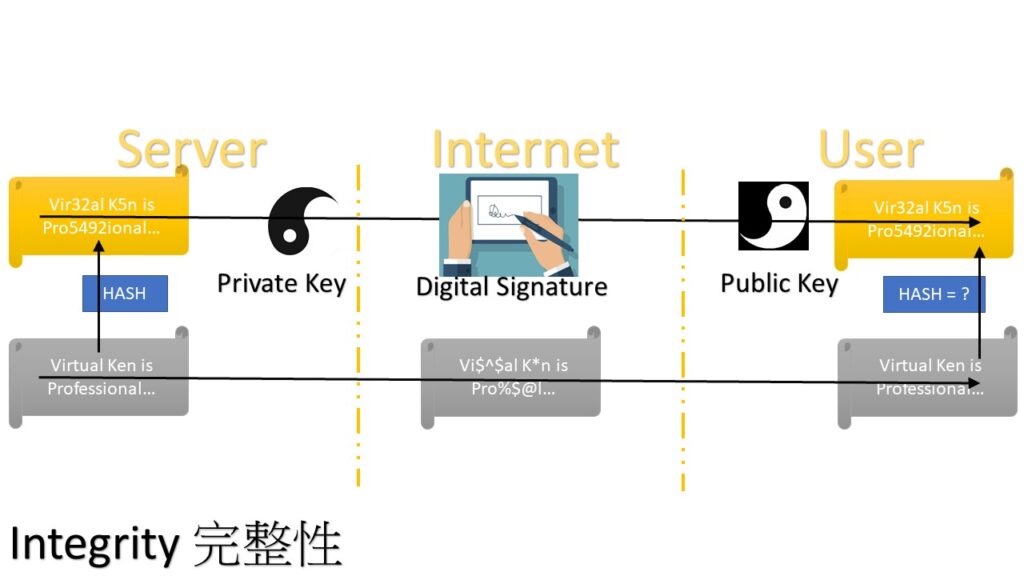
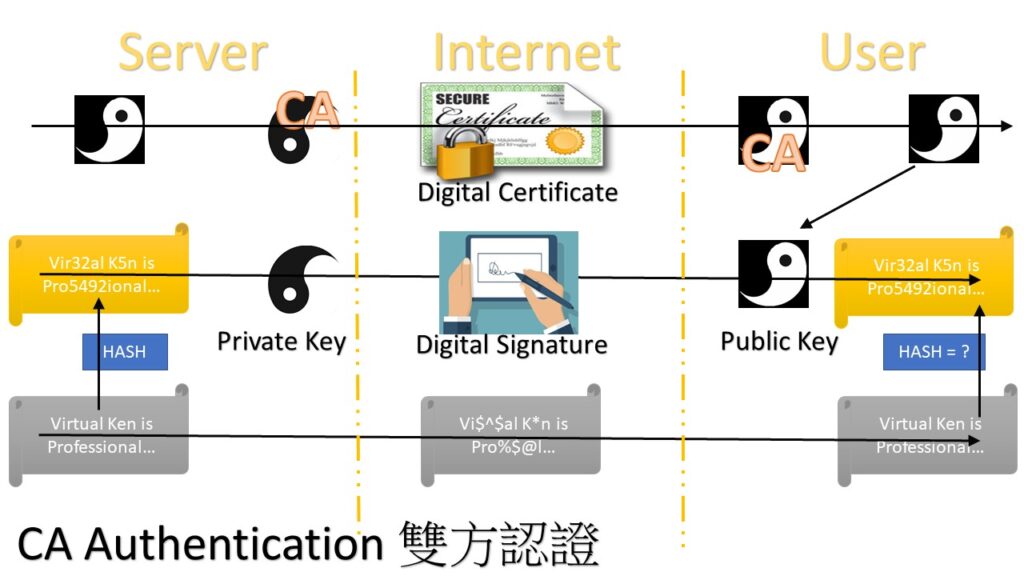
HTTPS:
Server 傳 certs先
Client 從 Cert中拿公Key 用作傳Sym Key
以Sym Key 通訊